Prepare for success with our comprehensive ACLs Test Questions and Answers 2022 guide. Dive into the fundamentals of Access Control Lists (ACLs), explore their implementation across operating systems, and master best practices for effective management. Whether you’re an IT professional or an aspiring security specialist, this guide will empower you with the knowledge and skills to excel in ACLs management.
Our in-depth coverage includes real-world examples, advanced ACLs concepts, and practical tools to streamline your ACLs management tasks. Enhance your understanding of inheritance, delegation, and auditing, and mitigate potential risks while maximizing the benefits of advanced ACLs features.
ACLs Test Questions and Answers 2022
Access Control Lists (ACLs) are security mechanisms that specify the permissions granted to users or groups for accessing and modifying resources within a computer system. ACLs define the level of access that each user or group has to a particular file, directory, or other system object.
ACLs are an essential part of any security system, as they allow administrators to control who has access to what and to what extent. ACLs can be used to grant or deny permissions for a wide range of operations, including reading, writing, executing, and deleting files and directories.
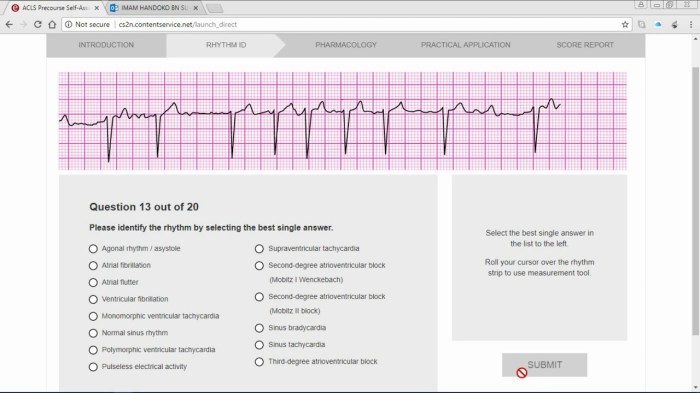
ACL Test Questions
The following is a comprehensive list of ACL test questions covering various topics related to ACLs:
- What is an Access Control List (ACL)?
- What are the different types of ACLs?
- How are ACLs used to control access to resources?
- What are the benefits of using ACLs?
- What are the challenges of managing ACLs?
ACL Test Answers
The following are sample ACL test answers with clear explanations:
- An Access Control List (ACL) is a security mechanism that specifies the permissions granted to users or groups for accessing and modifying resources within a computer system.
- There are two main types of ACLs: discretionary ACLs (DACLs) and system ACLs (SACLs). DACLs control access to resources based on the identity of the user or group, while SACLs control access to resources based on the type of access being requested.
- ACLs are used to control access to resources by defining the level of access that each user or group has to a particular file, directory, or other system object.
- The benefits of using ACLs include improved security, increased flexibility, and reduced administrative overhead.
- The challenges of managing ACLs include the complexity of ACLs, the difficulty of managing ACLs across multiple systems, and the potential for ACLs to be compromised.
ACLs for Different Operating Systems
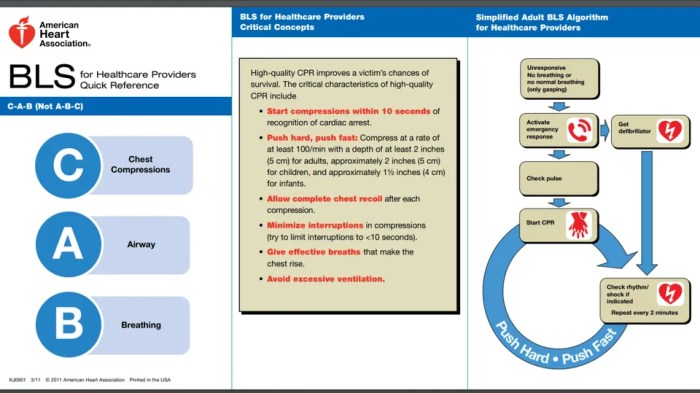
Access Control Lists (ACLs) are security mechanisms that restrict access to resources based on the identity of the user or group. Different operating systems implement ACLs in varying ways, offering unique features and functionalities.
Windows ACLs
- Windows ACLs are Discretionary Access Control Lists (DACLs), meaning they are managed by the owner of the resource.
- DACLs specify the permissions granted or denied to specific users or groups.
- Windows ACLs can be applied to files, folders, registry keys, and other system objects.
Linux ACLs
- Linux ACLs are both DACLs and Role-Based Access Control Lists (RBACLs).
- DACLs are similar to Windows ACLs, controlling access based on user or group identity.
- RBACLs allow access to be granted based on the role of the user or group, providing greater flexibility.
- Linux ACLs can be applied to files, directories, and other file system objects.
macOS ACLs
- macOS ACLs are similar to Linux RBACLs, allowing access to be granted based on user, group, or role.
- macOS ACLs are more granular than Windows or Linux ACLs, providing finer control over access permissions.
- macOS ACLs can be applied to files, folders, and other system objects.
Comparison of ACLs
| Feature | Windows ACLs | Linux ACLs | macOS ACLs |
|---|---|---|---|
| Type | DACLs | DACLs and RBACLs | RBACLs |
| Granularity | Less granular | More granular | Most granular |
| Flexibility | Limited | Moderate | High |
| Common Use Cases | File and folder permissions | File system and network resource permissions | File system, network resource, and application permissions |
Best Practices for ACLs Management

Effective ACLs management involves implementing best practices to ensure the integrity and security of access controls. These practices include:
Setting Up ACLs, Acls test questions and answers 2022
- Establishing clear and concise ACLs that define access permissions for users and groups.
- Assigning permissions based on the principle of least privilege, granting only the necessary level of access to each entity.
- Regularly reviewing and updating ACLs to reflect changes in user roles and responsibilities.
Modifying ACLs
- Using a systematic approach to modify ACLs, ensuring changes are authorized and documented.
- Implementing change control procedures to prevent unauthorized modifications.
- Maintaining a central repository for ACLs to facilitate management and auditing.
Revoking ACLs
- Promptly revoking ACLs when users or groups no longer require access.
- Implementing mechanisms to automatically revoke ACLs based on predefined criteria, such as user termination or group membership changes.
- Monitoring ACLs to identify any unauthorized access or modifications.
Auditing and Monitoring ACLs
- Regularly auditing ACLs to ensure compliance with security policies and regulations.
- Using tools and techniques to monitor ACLs for suspicious activity or unauthorized changes.
- Establishing an incident response plan to address any identified security breaches related to ACLs.
Advanced ACLs Concepts
Advanced ACLs features provide granular control over file and folder permissions, enhancing security and flexibility in ACLs management. These concepts include inheritance, delegation, and auditing, each offering unique capabilities and considerations.
Inheritance
Inheritance allows permissions granted to a parent folder or directory to be automatically inherited by its child objects, such as files and subfolders. This simplifies ACLs management by eliminating the need to set permissions individually for each child object. Inheritance can be configured to flow down or up the directory tree, providing flexibility in permission assignment.
Delegation
Delegation enables administrators to grant specific permissions to other users or groups, allowing them to manage ACLs on behalf of the administrator. This can be useful for delegating authority and responsibility for managing permissions in large or complex environments. Delegation can be configured to grant full control or specific permissions, ensuring appropriate levels of access.
Auditing
Auditing allows administrators to track and log changes made to ACLs, providing a record of who made the changes, when they were made, and what permissions were modified. This information can be valuable for security audits, compliance reporting, and troubleshooting permission issues.
Auditing can be configured to log all ACL changes or specific changes based on user or permission criteria.
Potential Risks and Benefits of Advanced ACLs Features
While advanced ACLs features provide enhanced control and flexibility, they also come with potential risks and benefits that should be considered:
- Risks:
- Complexity:Advanced ACLs features can introduce complexity into ACLs management, making it more challenging to understand and maintain.
- Inconsistent Permissions:Inheritance and delegation can lead to inconsistent permissions across objects, potentially creating security vulnerabilities.
- Over-privileging:Delegation can grant excessive permissions to users, increasing the risk of unauthorized access.
- Benefits:
- Granular Control:Advanced ACLs features provide granular control over permissions, allowing administrators to tailor access to specific users or groups.
- Simplified Management:Inheritance can simplify ACLs management by eliminating the need to set permissions for each child object.
- Improved Security:Auditing provides visibility into ACL changes, enabling administrators to identify and mitigate potential security threats.
Tools for ACLs Management
Efficient ACLs management requires specialized tools to streamline tasks, enhance security, and ensure compliance. These tools offer various features and capabilities, catering to specific ACLs management needs.
When selecting an ACLs management tool, consider factors such as the operating system, the scale of the environment, the level of automation desired, and the budget. Different tools may excel in different areas, so it’s crucial to evaluate their strengths and weaknesses before making a decision.
Comparison of ACLs Management Tools
- Native OS Tools:Operating systems often provide built-in tools for managing ACLs, such as the ‘setfacl’ and ‘getfacl’ commands in Linux and the ‘icacls’ command in Windows. These tools offer basic ACLs management capabilities but may lack advanced features and automation options.
- Third-Party Commercial Tools:Commercial ACLs management tools provide a comprehensive suite of features, including centralized management, automated workflows, auditing and reporting, and support for multiple operating systems. Examples include Varonis DatAdvantage, ManageEngine ADManager Plus, and Netwrix Auditor.
- Open-Source Tools:Open-source ACLs management tools offer a cost-effective alternative to commercial tools. They provide essential ACLs management capabilities but may lack the advanced features and support found in commercial offerings. Examples include ACL Manager for Windows and Facl for Linux.
Answers to Common Questions
What are Access Control Lists (ACLs)?
ACLs are security mechanisms that define who can access specific resources, such as files, directories, or network services, and what actions they can perform on those resources.
How do ACLs differ across operating systems?
Different operating systems implement ACLs with varying features and functionalities. For example, Windows ACLs support inheritance and auditing, while Linux ACLs provide more granular control over permissions.
What are best practices for managing ACLs effectively?
Best practices include using strong passwords, limiting access to sensitive data, regularly reviewing and updating ACLs, and implementing auditing mechanisms to monitor ACLs activity.